Crypto’Graph: Leveraging Privacy-Preserving Distributed Link Prediction for Robust Graph Learning
Sofiane Azogagh, Zelma Aubin Birba, Sébastien Gambs, and 1 more author
In Proceedings of the Fourteenth ACM Conference on Data and Application Security and Privacy, 2024
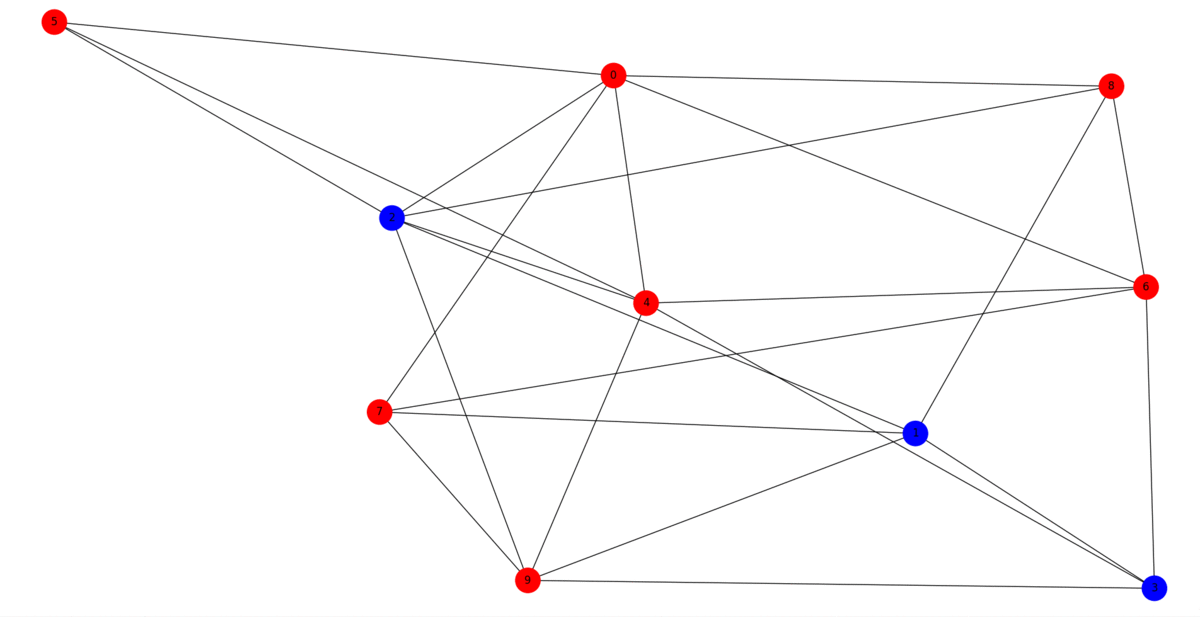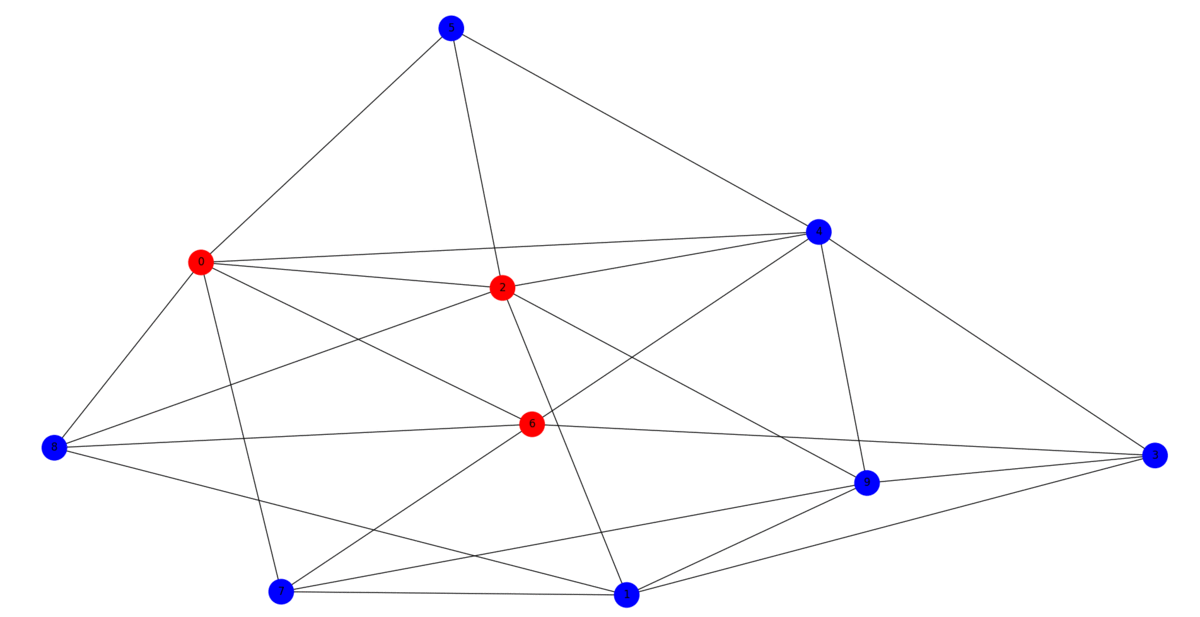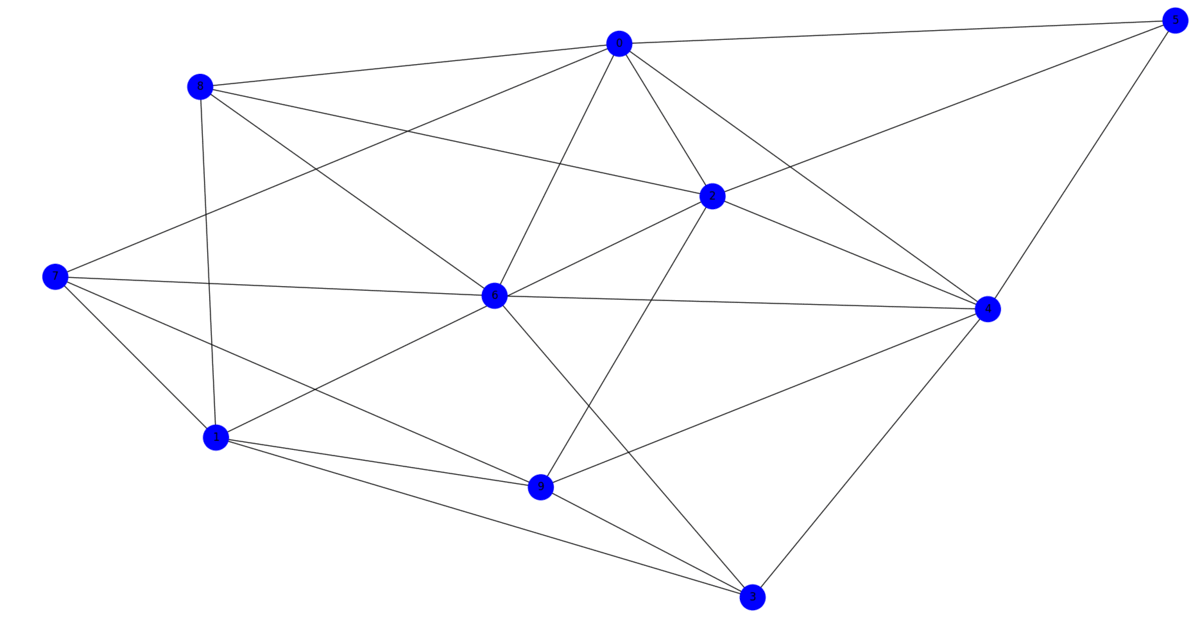
Graphs are a widely used data structure for collecting and analyzing relational data. However, when the graph structure is distributed across several parties, its analysis is challenging. In particular, due to the sensitivity of the data each party might want to keep their partial knowledge of the graph private, while still be willing to collaborate with the other parties for tasks of mutual benefit, such as data curation or the removal of poisoned data. To address this challenge, we propose Crypto’Graph, an efficient protocol for privacy-preserving link prediction on distributed graphs. More precisely, it allows parties partially sharing a graph with distributed links to infer the likelihood of formation of new links in the future. Through the use of cryptographic primitives, Crypto’Graph is able to compute the likelihood of these new links on the joint network without revealing the structure of the private graph of each party, even though they know the number of nodes they have, since they share the same graph in terms of nodes but not the same links. Crypto’Graph improves on previous works by enabling the computation of a diverse set of similarity metrics in parallel without any additional cost. The use of Crypto’Graph is illustrated for defense against graph poisoning attacks, in which potential adversarial links are identified without compromising the privacy of the graphs of individual parties. The effectiveness of Crypto’Graph in mitigating graph poisoning attacks and achieving high prediction accuracy on a node classification task using graph neural networks is demonstrated through extensive experimentation on two real-world datasets.
 From provable security to practical failure : What cryptography enables - and what it cannot prevent - in distributed graph learning2026
From provable security to practical failure : What cryptography enables - and what it cannot prevent - in distributed graph learning2026